Today, I had a long customer call. Cyberoam was very slow and was not reacting on the GUI menu click. The internet browsing was very slow. Total download bandwidth which was allotted to customer by ISP was around 15 Mbps but it was showing only 5 Mbps, when speedtest was done. Below is logical flow of the troubleshooting path which helped me to troubleshooting and resolve the issue:
==============================================================
Note: First create a plain firewall rule for a single IP address (LAN IP) and then check if behavior persists. If behavior persists then follow below steps. If not then there is some policy error applied on the firewall rule. Usually an IPS policy. Try fine tuning the IPS policy. We can fine tune an IPS policy by removing unwanted signatures for example, there is no need to scan traffic for FTP vulnerabilities if the actual server hosted is SMTP.
==============================================================
1> Searching for brute force attack from WAN:
Browse through Logs & Reports > Log Viewer > Admin Logs. Checked there were lot of failed admin login attempts.
Action: Disabled WAN access on port 23 (telnet) and port 22 (SSH), both TCP. Disabled the WAN access to the Cyberoam on port 80 (HTTP). We can do this by browsing through
System> Administration> Appliance access (TAB).
2> DOS Attack:
Enabled the DOS settings and we could see lot of ICMP flood. We found that it was a users laptop in the LAN which was generating too much of traffic. Administrator helped us to remove the PC from the network as primary mitigation attempt. ( I will discuss in another blog how to check if any PC in infected and what are the steps to be used as process for security incident)
3> Still, the speed stuck at 5Mbps. Now I wanted to check if the application classification was causing the trouble. I have then disabled the application classification settings from CLI
Command: cyberoam application_classification off
4> Still, the same behavior 5 Mbps. Now it was to check the MSS settings.
Theory of MSS and MTU: http://cyberoamexpert.blogspot.in/2012/02/mss-and-mtu.html
I started a tcpdump from the CLI for a particular IP on port 80 (Try TCP ports)
console> tcpdump "host 203.**.**.*** and port 80"
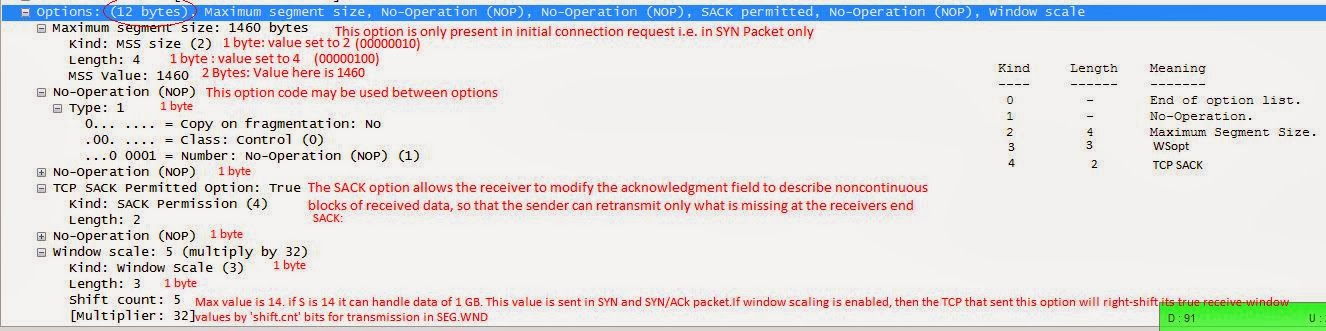
From an internal PC behind Cyberoam, we tried to telnet on 80 for IP 203.**.**.*** and we found below MSS values
First Packet : A SYN packet
07:11:33.546865 PortB_PPP, OUT: IP 184.**.***.*.48500 > 203.**.**.***.80: Flags [S], seq 1143423923, win 5840, options [
mss 1460,nop,nop,sackOK,nop,wscale 5], length 0
Reply packet : A SYN/ACK
07:11:33.800460 PortB_PPP, IN: IP 203.**.**.***.80 > 184.**.***.*.48500: Flags [S.], seq 2495986521, ack 1143423924, win 14600, options [
mss 1376,nop,nop,sackOK,nop,wscale 7], length 0
(I am going to add a new blog on understanding the TCP in more depth soon)
The highlighted values should match. We have changed the MSS values on port B of the Cyberoam from GUI Network> interfaces> Advanced settings> overide MSS
Speed went from 5Mbps to 14.86Mbps and thus resolving the issue.