As promised, here is how you can interpret TCPdump on Cyberoam. In this article I am going to change the source IP as SRC and destination IP ad DST.
1> A TCP packet on port 80 : A simple TCP handshake
console> tcpdump "host DST and port 80
tcpdump: Starting Packet Dump
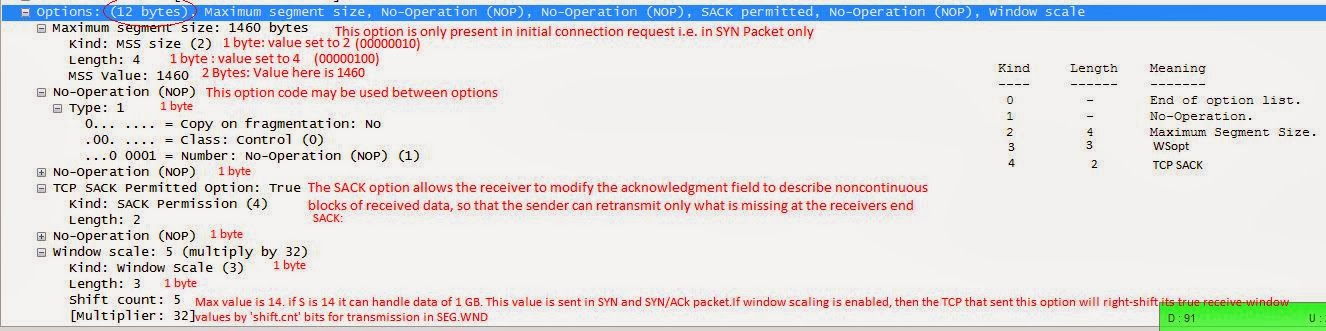
07:11:33.546865 PortB, OUT: IP SRC.48500 > DST.80: Flags [S], seq 1143423923, win 5840, options [mss 1460,nop,nop,sackOK,nop,wscale 5], length 0
07:11:33.800460 PortB, IN: IP DST.80 > SRC.48500: Flags [S.], seq 2495986521, ack 1143423924, win 14600, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:11:33.800545 PortB, OUT: IP SRC.48500 > DST.80: Flags [.], ack 1, win 183, length 0
I will explain the first packet and there after it will be easy for understanding the other packets:
07:11:33.546865 PortB, OUT: IP SRC.48500 > DST.80: Flags [S], seq 1143423923, win 5840, options [mss 1460,nop,nop,sackOK,nop,wscale 5], length 0
Will try to add my 2 cents on windows scaling in next blog