I am a great fan of UTM devices that give complete and granular control over different layer 7 application. Cyberoam is one of the best Application control UTM. In one of my previous articles named A Fight for the best application filter, I mentioned about the fact that how applications have changed over the years but we have not seen any significant change in firewall.
Coming on to the Cyberoam, it is feature rich product and I can feel the kind of effort being put in cyberoam into making it a world-class product. Now, they have come up with improved application control features. Now, we have a new way by which Cyberoam has categorized different applications. I really liked this improvement. Cyberoam represents applications in accordance to:
1. Name
2. Category
3. Risk
4. Characteristics
5. Technology
Here is the screenshot:
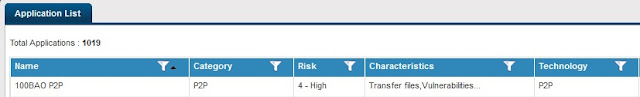 This will provide more granular control for the users over the applications. I believe, this was a long pending feature, and at last we have it. Cyberoam can identify over 1000 applications which is better than some other UTMs,
This will provide more granular control for the users over the applications. I believe, this was a long pending feature, and at last we have it. Cyberoam can identify over 1000 applications which is better than some other UTMs,
With the improvement in the categorization, the reporting feature has also seen lot changes.
Reporting has always been one of the best features of Cyberoam. You really have to work on a Cyberoam UTM device in order to really feel what power it holds. The on appliance iview is one of the best Reporting system. It has an hawk eye and provide you drill down reports upto 3rd level for forensic analysis. The new reporting system is more faster and eye catchier with its instant horizonal, vertical and pie chart representation of the logs.
Coming on to the Cyberoam, it is feature rich product and I can feel the kind of effort being put in cyberoam into making it a world-class product. Now, they have come up with improved application control features. Now, we have a new way by which Cyberoam has categorized different applications. I really liked this improvement. Cyberoam represents applications in accordance to:
1. Name
2. Category
3. Risk
4. Characteristics
5. Technology
Here is the screenshot:
 This will provide more granular control for the users over the applications. I believe, this was a long pending feature, and at last we have it. Cyberoam can identify over 1000 applications which is better than some other UTMs,
This will provide more granular control for the users over the applications. I believe, this was a long pending feature, and at last we have it. Cyberoam can identify over 1000 applications which is better than some other UTMs,With the improvement in the categorization, the reporting feature has also seen lot changes.
Reporting has always been one of the best features of Cyberoam. You really have to work on a Cyberoam UTM device in order to really feel what power it holds. The on appliance iview is one of the best Reporting system. It has an hawk eye and provide you drill down reports upto 3rd level for forensic analysis. The new reporting system is more faster and eye catchier with its instant horizonal, vertical and pie chart representation of the logs.